NoScript Security Suite by Giorgio Maone
The best security you can get in a web browser! Allow potentially malicious web content to run only from sites you trust. Protect yourself against XSS other web security exploits.
Available on Firefox for Android™Available on Firefox for Android™
257,697 Users257,697 Users
Extension Metadata
Screenshots
About this extension
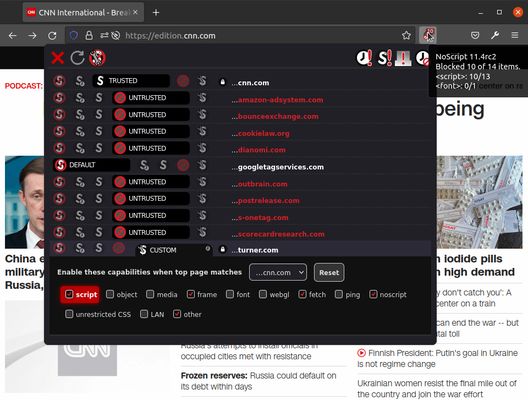
Winner of the "PC World - World Class Award" and bundled with the Tor Browser, NoScript gives you the best available protection on the web. It allows JavaScript, Flash, and other executable content to run only from trusted domains of your choice (e.g. your banking site), thus mitigating remotely exploitable vulnerabilities, such as Spectre and Meltdown.
It protects your "trust boundaries" against cross-site scripting attacks (XSS), cross-zone DNS rebinding / CSRF attacks (router hacking), and Clickjacking attempts, thanks to its unique ClearClick technology.
Such a preemptive approach prevents exploitation of security vulnerabilities (known and unknown!) with no loss of functionality where you need it.
Experts do agree: Firefox is really safer with NoScript!
FAQ: https://noscript.net/faq
Forum: https://noscript.net/forum
A Basic NoScript 10 Guide
Still confused by NoScript 10's new UI?
Check this user-contributed NoScript 10 primer.
and this NoScript 10 "Quantum" vs NoScript 5 "Classic" (or "Legacy") comparison.
It protects your "trust boundaries" against cross-site scripting attacks (XSS), cross-zone DNS rebinding / CSRF attacks (router hacking), and Clickjacking attempts, thanks to its unique ClearClick technology.
Such a preemptive approach prevents exploitation of security vulnerabilities (known and unknown!) with no loss of functionality where you need it.
Experts do agree: Firefox is really safer with NoScript!
FAQ: https://noscript.net/faq
Forum: https://noscript.net/forum
A Basic NoScript 10 Guide
Still confused by NoScript 10's new UI?
Check this user-contributed NoScript 10 primer.
and this NoScript 10 "Quantum" vs NoScript 5 "Classic" (or "Legacy") comparison.
Security issues affecting Firefox or the Tor Browser which can be fixed by a NoScript update are guaranteed to be addressed within 24 hours. This sometimes requires many updates to be issued in a short timespan, and when this happens you may notice NoScript UI's asking to "reload this page in order to operate properly". This is normal on "live" updates, and it just means the UI is out of sync with the page content, but there's no need to worry as all the restrictions to scripts and active content are still in place.
Rated 4.4 by 2,422 reviewers
Permissions and data
Required permissions:
- Access browser tabs
- Access browser activity during navigation
- Access your data for all websites
More information
- Add-on Links
- Version
- 13.5.12
- Size
- 831.03 KB
- Last updated
- a month ago (Jan 24, 2026)
- Related Categories
- Privacy Policy
- Read the privacy policy for this add-on
- Version History
- Add to collection
The developer of this extension asks that you help support its continued development by making a small contribution.