Web Security Audit sɣur Francesco De Stefano
Passively audits the security posture on current page
67 yiseqdacen67 yiseqdacen
Asiɣzef aɣefisefka
Tuṭṭfiwin n wegdil
Ɣef usiɣzef agi
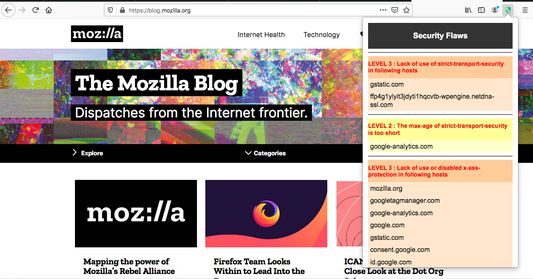
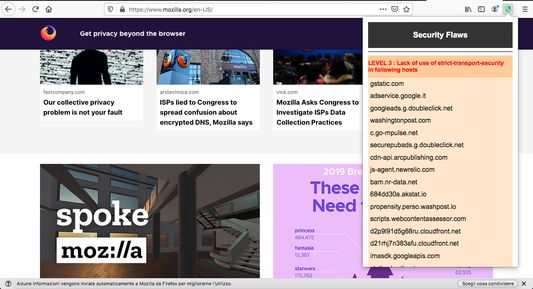
The goal of this project is to build an add-on for browser that passively audits the security posture of the websites that the user is visiting. Assume that the tool is to be used on non-malicious websites, currently not under attack or compromised. Add-on wants to report security misconfigurations, or failure to use best security practices.
- Add-on tries to analysis the commonly vulnerable setting of servers: lack of use of security-relevant headers, including:
- strict-transport-security
- x-xss-protection
- content-security-policy
- x-frame-options
- x-content-type-options
- It doesn't to interfere with the functioning of the visited website.
- It doesn't tamper with request parameters, or issue requests that were not initiated by the user (it is not active scanning).
- Incrementally generate a report in a separate window.
- Each report entry have a numeric score to indicate approximately its severity, as a way to prioritise further investigation by a human analyst [Common Vulnerability Scoring System](https://en.wikipedia.org/wiki/Common_Vulnerability_Scoring_System).
### Limitations
- Add-on only works on sites that allow content scripts.
- Add-on tries to analysis the commonly vulnerable setting of servers: lack of use of security-relevant headers, including:
- strict-transport-security
- x-xss-protection
- content-security-policy
- x-frame-options
- x-content-type-options
- It doesn't to interfere with the functioning of the visited website.
- It doesn't tamper with request parameters, or issue requests that were not initiated by the user (it is not active scanning).
- Incrementally generate a report in a separate window.
- Each report entry have a numeric score to indicate approximately its severity, as a way to prioritise further investigation by a human analyst [Common Vulnerability Scoring System](https://en.wikipedia.org/wiki/Common_Vulnerability_Scoring_System).
### Limitations
- Add-on only works on sites that allow content scripts.
Rated 5 by 5 reviewers
Tisirag akked yisefka
Ugar n telɣut
- TigIseɣwan n uzegrir
- Lqem
- 1.0
- Teɣzi
- 24,75 KB
- Aleqqem aneggaru
- för 6 år sedan (13 feb 2020)
- Taggayin i ilan assaɣ
- Amazray n Lqem
- Rnu ar tegrumma
Aneflay n usiɣzef-agi isutur-ak-d tallelt akken ad iseddu taneflit ines ticki tmuddeḍ-as cwiṭ n tewsa.