Tracy wót Jake Heath
A tool designed to assist with finding all sinks and sources of a web application and display these results in a digestible manner.
7 wužywarjow7 wužywarjow
Metadaty rozšyrjenja
Fota wobrazowki
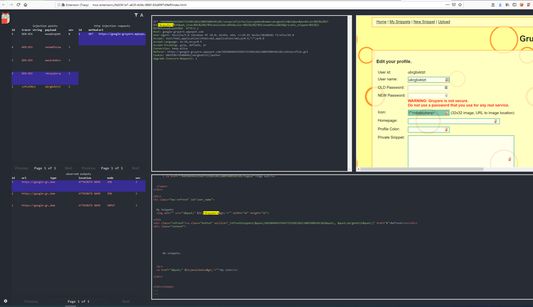
Wó toś tom rozšyrjenju
A tool designed to assist with finding all sinks and sources of a web application and display these results in a digestible manner.
There are many different ways to trigger XSS, especially considering the large number of frontend frameworks that have been made popular in the last few years. For example, some of the less traditional ways of exploiting XSS can be through:
These attack vectors are significantly different than traditional stored and reflected XSS cases and they require new tools for finding them effectively.
Many similar tools only look for server response reflection, however this is not very helpful if all output encoding is performed by the frontend. In order to really gain knowledge about all the true sinks of the application, we need a tool that grants us "X-ray vision into the DOM".
This extensions was written with the goal of eliminating XSS by assisting a penetration tester in identifying every source of input into an application and following that input to all of its sinks. These cases are documented and stored as references that can be used to identify the locations of potentially risky input.
There are many different ways to trigger XSS, especially considering the large number of frontend frameworks that have been made popular in the last few years. For example, some of the less traditional ways of exploiting XSS can be through:
- DOM clobbering
- DOM injection
- Frontend template injection
- Backend template injection
- Open redirects
These attack vectors are significantly different than traditional stored and reflected XSS cases and they require new tools for finding them effectively.
Many similar tools only look for server response reflection, however this is not very helpful if all output encoding is performed by the frontend. In order to really gain knowledge about all the true sinks of the application, we need a tool that grants us "X-ray vision into the DOM".
This extensions was written with the goal of eliminating XSS by assisting a penetration tester in identifying every source of input into an application and following that input to all of its sinks. These cases are documented and stored as references that can be used to identify the locations of potentially risky input.
Z 5 wót 4 pógódnośujucych pógódnośony
Pšawa a daty
Dalšne informacije
- Dodankowe wótzkaze
- Wersija
- 0.9.2
- Wjelikosć
- 910,55 KB
- Slědny raz zaktualizěrowany
- 5 jierren lyn (21 mai 2021)
- Pśiswójźbne kategorije
- Licenca
- Licenca MIT
- Wersijowa historija
- Zběrce pśidaś